This article will explain How To Create A Wallet Drainer? To create a wallet drainer, you have to follow some tips. A brand-new wave of cryptocurrency drainers has descended onto the cryptosphere, wiping out wallets everywhere they go.
As of publication, these crypto drainers have stolen up to $60 million from several crypto wallets. But wait, what are crypto drainers in the first place? And how can one prevent them from falling for their tricks? For more information on crypto drainers, continue reading.
How To Create A Wallet Drainer?
There is no authentic procedure to create a wallet drainer, but I can tell you how you can operate it. Phishing pages called “Crypto Drainers” tempt victims into approving fraudulent transactions, which the attacker then uses to steal their crypto and NFTs.
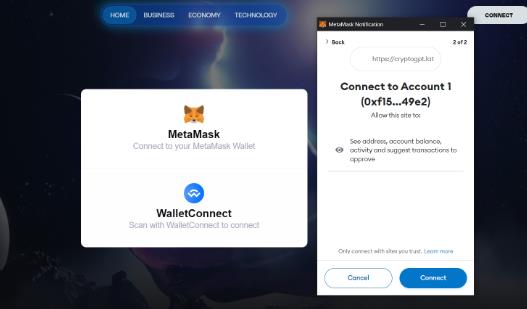
These websites frequently rely on well-known or newly launched NFT initiatives. Spam campaigns on social media and Discord are the main methods to advertise the websites.
The majority of crypto drainers operate in a rather simple manner:
- False NFT minting pages that use a fake countdown to imply urgency.
- The victim links “mint” to their wallet.
- Verify if the victim’s address owns any pricey NFTs.
- The victim authorizes the transfer of ownership of NFTs.
- The victim gives the attacker a transaction. However, this transaction is not a contract interaction for the price of the fictitious “mint.”
- Repeat after me.
What Are Crypto Drainers?
Crypto Drainers or Sweepers are harmful smart contracts that can quickly remove all the money from a Bitcoin wallet. The technology is ideal for phishing fraud.
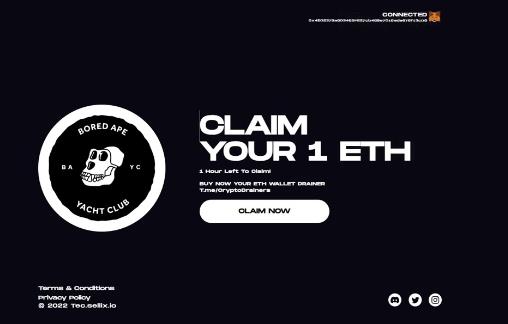
This Is How Cryptocurrency Drainers Operate
The wallet owner is duped into unintentionally consenting to a sinister transaction in the wallet. The kind of transaction agreed upon will allow the smart contract to transfer all or a portion of the wallet’s assets.
Then, the wallet’s contents are effortlessly deleted. Sad! Therefore, the sole purpose of a hacker utilizing a crypto drainer is to convince the wallet’s owner that the transaction being approved is real.
Once that goal has been accomplished, the hacker can do whatever they want with the wallet’s assets. With the Monkey Drainer fraud exposure in November 2022, bitcoin drainers began to increase.
Since then, the number of cryptocurrency drainer frauds has increased. According to Scam Sniffer, some of these crypto drainers are lent to phishing scam organizations. A fee is assessed for it.
Many cryptocurrency drainer owners charge additional costs for their drainers in addition to the commission they charge, and some even provide “add-ons” like fraudulent signature requests and other features.
In addition to Money Drainers, which ceased operations in February 2023, several other crypto drainers have been entering the market.
How To Safeguard Your Wallets From Crypto Drainers?
Following are some fundamental guidelines to protect your wallets from the threat of crypto drainers:

Tip 1 – Avoid Unidentifiable Links
Yes, shun any links whose source you cannot verify like the plague! Watch for links and advertisements that flash over the device screen when you complete a transaction. Before selecting any of them, could you closely examine them?
Tip 2 – Avoid Google Ads For Crypto Services
Go to the official website rather than the crypto sites’ advertisements. Don’t click on URLs in a rush; instead, pause to be sure you’re using the right one before you proceed. For instance, binance.com might be written as ‘biananc.com’ or ‘binancé.com.’
Tip 3 – Keep Funds In Multiple Wallets
It’s advised to avoid putting all of your eggs in one basket. For crypto, this is also accurate. Let’s imagine you have cryptocurrency assets worth $25,000 in total. It is suggested that you divide the money among several wallets.
Your money will be protected if you do this. In the unlikely event that one of the wallets is compromised, you will only lose a small amount of your investment.
Tip 4– Enable Two-Factor Authentication
Two-factor authentication, or 2FA, is an additional layer of security for cryptocurrency wallets. With it turned on, you can avoid these drainers even if they manage to get into your wallet. There is only one method to compromise your wallet if the 2FA code is known.
Tip 5 – Use Of Hardware Wallets
Hardware wallets remain offline, making them the safest sort of cryptocurrency wallet among the others. When your money is kept in a hardware wallet, crypto drainers have no chance against you as long as you safeguard your private keys and the device itself!
Ledger and Trezor wallets are two examples. Ultimately, it comes down to always being aware. Always be cautious whether you are conducting a trade or simply browsing the cryptocurrency streets.
What Are Different Types Of Cryptocurrency Wallets?
You can create a variety of wallets for cryptocurrencies. You can use them online, on a PC, or on a mobile device. They fall into three well-defined categories:
- Online software
- Equipment
- Paper

Types Of Cryptocurrency Wallets
Desktop
These wallets are downloaded as applications and installed on a computer or laptop. Additionally, they can only be accessed from the desktop where they were installed. Due to the lack of a browser, desktop wallets feature one of the highest degrees of protection available.
However, you could lose all your money if your computer is hacked, infected with a virus, or the wallet file becomes corrupted. If you decide on a desktop version, you must frequently back up the wallet to reduce the chance of losing the entire file.
Online
Wallets are quite practical because they are kept in the cloud and are simple to access from any location as long as you have an internet connection. But remember that since a third party controls them, they are not completely private.
Keep in mind that in addition to your money, you must also keep your private key there. Online wallets are, hence, more vulnerable to theft and hacker attempts.
Mobile
They are loaded as applications on your mobile device, and to use them and conduct transactions, you must have a strong 3G or Wi-Fi connection.
They frequently have less functionality than the desktop app but otherwise are identical. It will help if you exercise caution when utilizing them because they increase your vulnerability to hacking assaults, especially when using public Wi-Fi or open areas.
Hardware
The way the keys are stored differs between hardware and software wallets. Using a hardware wallet, you must keep your keys on a specific item, like a USB stick.
Although your money is stored offline, which increases security, you may still conduct transactions online exactly as you would with any other wallet.
Although offline, they are portable and simple to track. You must connect your device to a computer with an internet connection, enter a PIN, transmit money, and confirm to complete a transaction.
Paper
Given that one benefit of using virtual currency is the absence of paper money, these wallets may be the least popular. Your public and private keys are printed and placed in the paper wallet. The wallet’s printing considerably lowers security, and you risk misplacing the paper.
You still require a software wallet to transfer money using a paper wallet. Your paper wallet’s public address must be entered into the software wallet for money to transfer automatically.
You must transfer money from your paper wallet to your software wallet before you may withdraw it. Sweeping, also known as money transfer, can be carried out manually by entering your private keys or automatically by scanning the QR code on the paper wallet.
Are Cryptocurrency Wallets Secure?
Your choice of wallet and how carefully you handle the keys will determine the amount of security. If you use the cloud, online wallets are more susceptible to hacking and penetration by third parties. When this happens, hardware wallets appear more secure, and users of large sums of money frequently use them.
But since I barely ever do anything offline, it’s difficult to picture storing virtual currency offline. It also raises the bar of having to create a software account. You must use caution and safety measures!

You won’t be able to get your money back if you misplace any of the keys, lose your money, or fall victim to a cyberattack. If you choose to use an online wallet, it’s crucial to put the proper, meticulous security measures into place:
#1 Back Up Your Wallet
Combining a hardware and online wallet is one of the best pieces of advice I have ever heard. You can keep little sums you plan to use frequently and for modest payments in your online wallet.
At the same time, your hardware wallet can keep most of your money in a very secure setting. You need to remember to routinely back up your wallet, especially if it’s stored on a desktop computer or USB stick.
Ledger Wallet is one of the greatest services that provides a hardware and online wallet; after joining up, you can access the internet platform and a safe USB stick.
#2 Update Your Software
How many times have you heard of harmful software or hackers who gained access to your computer simply because you hadn’t updated to the most recent version of the operating system?
I recommend a fair amount. You can no longer ignore any of those unpleasant messages if you intend to invest in cryptocurrencies. It’s critical to offer the highest level of security.
#3 Pay Extra Attention To Your Passwords
We all know how simple it is to construct a simple password to remember, even though it may sound cliché. Traditional banks require you to enter lengthy passwords, complex PIN codes, and tokens for a reason.
They know how anxious hackers are to make one error and gain access to your entire account. In the same way, you must safeguard your password and cryptographic keys in Bitcoin wallets. Use wallets that offer additional security layers and have a strong reputation.
Conclusion
I hope you know about creating a wallet drainer. A crypto drainer is one of the newest frauds in the cryptocurrency world. But as with numerous other frauds, the best course of action is to exercise caution.
You will be safe outside if you take the essential safety measures. Even if there is an assault, the impact will be much reduced because of the safeguards taken.
Top FAQ’s
How do you drain a wallet?
A wallet is drained when your assets are transferred from your possession to the scammers. What makes it possible? So, a con artist can’t just hack into your highly protected private key and steal all your priceless NFTs; they need your permission to do that.
How do wallet drainers work?
Drainers deceive their victims into signing a fraudulent transaction. The victim’s money will be taken in this transaction by the drainer. The drainer may, for instance, send the victim a phishing email that appears to be from a reliable Bitcoin exchange.
What is a NFT drainer?
The FBI warns prospective purchasers of NFT to watch out for unscrupulous websites that employ “drainer smart contracts” to steal Bitcoin wallets covertly. The websites promote themselves as distribution channels for genuine NFT projects that offer fresh products.
What is a Metamask drainer?
Cryptocurrency can be moved from the victim’s wallet to the attacker using the Metamask private drainer.

Muhammad Talha Naeem is a seasoned finance professional with a wealth of practical experience in various niches of the financial world. With a career spanning over a decade, Talha has consistently demonstrated his expertise in navigating the complexities of finance, making him a trusted and reliable figure in the industry.